Deploy Azure File Sync with PowerShell
Deploy Azure File Sync with PowerShell
Deploy Azure File Sync | Microsoft Docs
Use Azure File Sync to centralize your organization's file shares in Azure Files, while keeping the flexibility, performance, and compatibility of an on-premises file server. Azure File Sync transforms Windows Server into a quick cache of your Azure file share. You can use any protocol that's available on Windows Server to access your data locally, including SMB, NFS, and FTPS. You can have as many caches as you need across the world.
We strongly recommend that you read Planning for an Azure Files deployment and Planning for an Azure File Sync deployment before you complete the steps described in this article.
Prerequisites
An Azure file share in the same region that you want to deploy Azure File Sync. For more information, see:
- Region availability for Azure File Sync.
- Create a file share for a step-by-step description of how to create a file share.
At least one supported instance of Windows Server or Windows Server cluster to sync with Azure File Sync. For more information about supported versions of Windows Server and recommended system resources, see Windows file server considerations.
The Az PowerShell module may be used with either PowerShell 5.1 or PowerShell 6+. You may use the Az PowerShell module for Azure File Sync on any supported system, including non-Windows systems, however the server registration cmdlet must always be run on the Windows Server instance you are registering (this can be done directly or via PowerShell remoting). On Windows Server 2012 R2, you can verify that you are running at least PowerShell 5.1.* by looking at the value of the PSVersion property of the $PSVersionTable object:
PowerShell$PSVersionTable.PSVersionIf your PSVersion value is less than 5.1.*, as will be the case with most fresh installations of Windows Server 2012 R2, you can easily upgrade by downloading and installing Windows Management Framework (WMF) 5.1. The appropriate package to download and install for Windows Server 2012 R2 is Win8.1AndW2K12R2-KB*******-x64.msu.
PowerShell 6+ can be used with any supported system, and can be downloaded via its GitHub page.
Important
If you plan to use the Server Registration UI, rather than registering directly from PowerShell, you must use PowerShell 5.1.
If you have opted to use PowerShell 5.1, ensure that at least .NET 4.7.2 is installed. Learn more about .NET Framework versions and dependencies on your system.
Important
If you are installing .NET 4.7.2+ on Windows Server Core, you must install with the
quietandnorestartflags or the installation will fail. For example, if installing .NET 4.8, the command would look like the following:PowerShellStart-Process -FilePath "ndp48-x86-x64-allos-enu.exe" -ArgumentList "/q /norestart" -WaitThe Az PowerShell module, which can be installed by following the instructions here: Install and configure Azure PowerShell.
Note
The Az.StorageSync module is now installed automatically when you install the Az PowerShell module.
Prepare Windows Server to use with Azure File Sync
For each server that you intend to use with Azure File Sync, including each server node in a Failover Cluster, disable Internet Explorer Enhanced Security Configuration. This is required only for initial server registration. You can re-enable it after the server has been registered.
To disable the Internet Explorer Enhanced Security Configuration, execute the following from an elevated PowerShell session:
$installType = (Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\").InstallationType
# This step is not required for Server Core
if ($installType -ne "Server Core") {
# Disable Internet Explorer Enhanced Security Configuration
# for Administrators
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A7-37EF-4b3f-8CFC-4F3A74704073}" -Name "IsInstalled" -Value 0 -Force
# Disable Internet Explorer Enhanced Security Configuration
# for Users
Set-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Active Setup\Installed Components\{A509B1A8-37EF-4b3f-8CFC-4F3A74704073}" -Name "IsInstalled" -Value 0 -Force
# Force Internet Explorer closed, if open. This is required to fully apply the setting.
# Save any work you have open in the IE browser. This will not affect other browsers,
# including Microsoft Edge.
Stop-Process -Name iexplore -ErrorAction SilentlyContinue
}
Deploy the Storage Sync Service
The deployment of Azure File Sync starts with placing a Storage Sync Service resource into a resource group of your selected subscription. We recommend provisioning as few of these as needed. You will create a trust relationship between your servers and this resource and a server can only be registered to one Storage Sync Service. As a result, it is recommended to deploy as many storage sync services as you need to separate groups of servers. Keep in mind that servers from different storage sync services cannot sync with each other.
Note
The Storage Sync Service inherits access permissions from the subscription and resource group it has been deployed into. We recommend that you carefully check who has access to it. Entities with write access can start syncing new sets of files from servers registered to this storage sync service and cause data to flow to Azure storage that is accessible to them.
Replace <Az_Region>, <RG_Name>, and <my_storage_sync_service> with your own values, then use the following commands to create and deploy a Storage Sync Service:
$hostType = (Get-Host).Name
if ($installType -eq "Server Core" -or $hostType -eq "ServerRemoteHost") {
Connect-AzAccount -UseDeviceAuthentication
}
else {
Connect-AzAccount
}
# this variable holds the Azure region you want to deploy
# Azure File Sync into
$region = '<Az_Region>'
# Check to ensure Azure File Sync is available in the selected Azure
# region.
$regions = @()
Get-AzLocation | ForEach-Object {
if ($_.Providers -contains "Microsoft.StorageSync") {
$regions += $_.Location
}
}
if ($regions -notcontains $region) {
throw [System.Exception]::new("Azure File Sync is either not available in the selected Azure Region or the region is mistyped.")
}
# the resource group to deploy the Storage Sync Service into
$resourceGroup = '<RG_Name>'
# Check to ensure resource group exists and create it if doesn't
$resourceGroups = @()
Get-AzResourceGroup | ForEach-Object {
$resourceGroups += $_.ResourceGroupName
}
if ($resourceGroups -notcontains $resourceGroup) {
New-AzResourceGroup -Name $resourceGroup -Location $region
}
$storageSyncName = "<my_storage_sync_service>"
$storageSync = New-AzStorageSyncService -ResourceGroupName $resourceGroup -Name $storageSyncName -Location $region
Install the Azure File Sync agent
The Azure File Sync agent is a downloadable package that enables Windows Server to be synced with an Azure file share.
Execute the following PowerShell code to download the appropriate version of the Azure File Sync agent for your OS and install it on your system.
Important
If you intend to use Azure File Sync with a Failover Cluster, the Azure File Sync agent must be installed on every node in the cluster. Each node in the cluster must registered to work with Azure File Sync.
# Gather the OS version
$osver = [System.Environment]::OSVersion.Version
# Download the appropriate version of the Azure File Sync agent for your OS.
if ($osver.Equals([System.Version]::new(10, 0, 17763, 0))) {
Invoke-WebRequest `
-Uri https://aka.ms/afs/agent/Server2019 `
-OutFile "StorageSyncAgent.msi"
} elseif ($osver.Equals([System.Version]::new(10, 0, 14393, 0))) {
Invoke-WebRequest `
-Uri https://aka.ms/afs/agent/Server2016 `
-OutFile "StorageSyncAgent.msi"
} elseif ($osver.Equals([System.Version]::new(6, 3, 9600, 0))) {
Invoke-WebRequest `
-Uri https://aka.ms/afs/agent/Server2012R2 `
-OutFile "StorageSyncAgent.msi"
} else {
throw [System.PlatformNotSupportedException]::new("Azure File Sync is only supported on Windows Server 2012 R2, Windows Server 2016, and Windows Server 2019")
}
# Install the MSI. Start-Process is used to PowerShell blocks until the operation is complete.
# Note that the installer currently forces all PowerShell sessions closed - this is a known issue.
Start-Process -FilePath "StorageSyncAgent.msi" -ArgumentList "/quiet" -Wait
# Note that this cmdlet will need to be run in a new session based on the above comment.
# You may remove the temp folder containing the MSI and the EXE installer
Remove-Item -Path ".\StorageSyncAgent.msi" -Recurse -Force
Register Windows Server with Storage Sync Service
Registering your Windows Server with a Storage Sync Service establishes a trust relationship between your server (or cluster) and the Storage Sync Service. A server can only be registered to one Storage Sync Service and can sync with other servers and Azure file shares associated with the same Storage Sync Service.
Note
Server registration uses your Azure credentials to create a trust relationship between the Storage Sync Service and your Windows Server, however subsequently the server creates and uses its own identity that is valid as long as the server stays registered and the current Shared Access Signature token (Storage SAS) is valid. A new SAS token cannot be issued to the server once the server is unregistered, thus removing the server's ability to access your Azure file shares, stopping any sync.
The administrator registering the server must be a member of the management roles Owner or Contributor for the given Storage Sync Service. This can be configured under Access Control (IAM) in the Azure portal for the Storage Sync Service.
It is also possible to differentiate administrators able to register servers from those allowed to also configure sync in a Storage Sync Service. For that you would need to create a custom role where you list the administrators that are only allowed to register servers and give your custom role the following permissions:
- "Microsoft.StorageSync/storageSyncServices/registeredServers/write"
- "Microsoft.StorageSync/storageSyncServices/read"
- "Microsoft.StorageSync/storageSyncServices/workflows/read"
- "Microsoft.StorageSync/storageSyncServices/workflows/operations/read"
$registeredServer = Register-AzStorageSyncServer -ParentObject $storageSync
Create a sync group and a cloud endpoint
A sync group defines the sync topology for a set of files. Endpoints within a sync group are kept in sync with each other. A sync group must contain one cloud endpoint, which represents an Azure file share and one or more server endpoints. A server endpoint represents a path on a registered server. A server can have server endpoints in multiple sync groups. You can create as many sync groups as you need to appropriately describe your desired sync topology.
A cloud endpoint is a pointer to an Azure file share. All server endpoints will sync with a cloud endpoint, making the cloud endpoint the hub. The storage account for the Azure file share must be located in the same region as the Storage Sync Service. The entirety of the Azure file share will be synced, with one exception: A special folder, comparable to the hidden "System Volume Information" folder on an NTFS volume, will be provisioned. This directory is called ".SystemShareInformation". It contains important sync metadata that will not sync to other endpoints. Do not use or delete it!
Important
You can make changes to any cloud endpoint or server endpoint in the sync group and have your files synced to the other endpoints in the sync group. If you make a change to the cloud endpoint (Azure file share) directly, changes first need to be discovered by an Azure File Sync change detection job. A change detection job is initiated for a cloud endpoint only once every 24 hours. For more information, see Azure Files frequently asked questions.
The administrator creating the cloud endpoint must be a member of the management role Owner for the storage account that contains the Azure file share the cloud endpoint is pointing to. This can be configured under Access Control (IAM) in the Azure portal for the storage account.
To create the sync group, execute the following PowerShell. Remember to replace <my-sync-group> with the desired name of the sync group.
$syncGroupName = "<my-sync-group>"
$syncGroup = New-AzStorageSyncGroup -ParentObject $storageSync -Name $syncGroupName
Once the sync group has been successfully created, you can create your cloud endpoint. Be sure to replace <my-storage-account> and <my-file-share> with the expected values.
# Get or create a storage account with desired name
$storageAccountName = "<my-storage-account>"
$storageAccount = Get-AzStorageAccount -ResourceGroupName $resourceGroup | Where-Object {
$_.StorageAccountName -eq $storageAccountName
}
if ($storageAccount -eq $null) {
$storageAccount = New-AzStorageAccount `
-Name $storageAccountName `
-ResourceGroupName $resourceGroup `
-Location $region `
-SkuName Standard_LRS `
-Kind StorageV2 `
-EnableHttpsTrafficOnly:$true
}
# Get or create an Azure file share within the desired storage account
$fileShareName = "<my-file-share>"
$fileShare = Get-AzStorageShare -Context $storageAccount.Context | Where-Object {
$_.Name -eq $fileShareName -and $_.IsSnapshot -eq $false
}
if ($fileShare -eq $null) {
$fileShare = New-AzStorageShare -Context $storageAccount.Context -Name $fileShareName
}
# Create the cloud endpoint
New-AzStorageSyncCloudEndpoint `
-Name $fileShare.Name `
-ParentObject $syncGroup `
-StorageAccountResourceId $storageAccount.Id `
-AzureFileShareName $fileShare.Name
Create a server endpoint
A server endpoint represents a specific location on a registered server, such as a folder on a server volume. A server endpoint is subject to the following conditions:
- A server endpoint must be a path on a registered server (rather than a mounted share). Network attached storage (NAS) is not supported.
- Although the server endpoint can be on the system volume, server endpoints on the system volume may not use cloud tiering.
- Changing the path or drive letter after you established a server endpoint on a volume is not supported. Make sure you are using a final path on your registered server.
- A registered server can support multiple server endpoints, however a sync group can only have one server endpoint per registered server at any given time. Other server endpoints within the sync group must be on different registered servers.
Execute the following PowerShell commands to create the server endpoint, and be sure to replace <your-server-endpoint-path>, <your-volume-free-space> with the desired values and check the settings for the optional initial download and initial upload policies.
$serverEndpointPath = "<your-server-endpoint-path>"
$cloudTieringDesired = $true
$volumeFreeSpacePercentage = <your-volume-free-space>
# Optional property. Choose from: [NamespaceOnly] default when cloud tiering is enabled. [NamespaceThenModifiedFiles] default when cloud tiering is disabled. [AvoidTieredFiles] only available when cloud tiering is disabled.
$initialDownloadPolicy = "NamespaceOnly"
$initialUploadPolicy = "Merge"
# Optional property. Choose from: [Merge] default for all new server endpoints. Content from the server and the cloud merge. This is the right choice if one location is empty or other server endpoints already exist in the sync group. [ServerAuthoritative] This is the right choice when you seeded the Azure file share (e.g. with Data Box) AND you are connecting the server location you seeded from. This enables you to catch up the Azure file share with the changes that happened on the local server since the seeding.
if ($cloudTieringDesired) {
# Ensure endpoint path is not the system volume
$directoryRoot = [System.IO.Directory]::GetDirectoryRoot($serverEndpointPath)
$osVolume = "$($env:SystemDrive)\"
if ($directoryRoot -eq $osVolume) {
throw [System.Exception]::new("Cloud tiering cannot be enabled on the system volume")
}
# Create server endpoint
New-AzStorageSyncServerEndpoint `
-Name $registeredServer.FriendlyName `
-SyncGroup $syncGroup `
-ServerResourceId $registeredServer.ResourceId `
-ServerLocalPath $serverEndpointPath `
-CloudTiering `
-VolumeFreeSpacePercent $volumeFreeSpacePercentage `
-InitialDownloadPolicy $initialDownloadPolicy `
-InitialUploadPolicy $initialUploadPolicy
} else {
# Create server endpoint
New-AzStorageSyncServerEndpoint `
-Name $registeredServer.FriendlyName `
-SyncGroup $syncGroup `
-ServerResourceId $registeredServer.ResourceId `
-ServerLocalPath $serverEndpointPath `
-InitialDownloadPolicy $initialDownloadPolicy
}
Configure firewall and virtual network settings
Portal
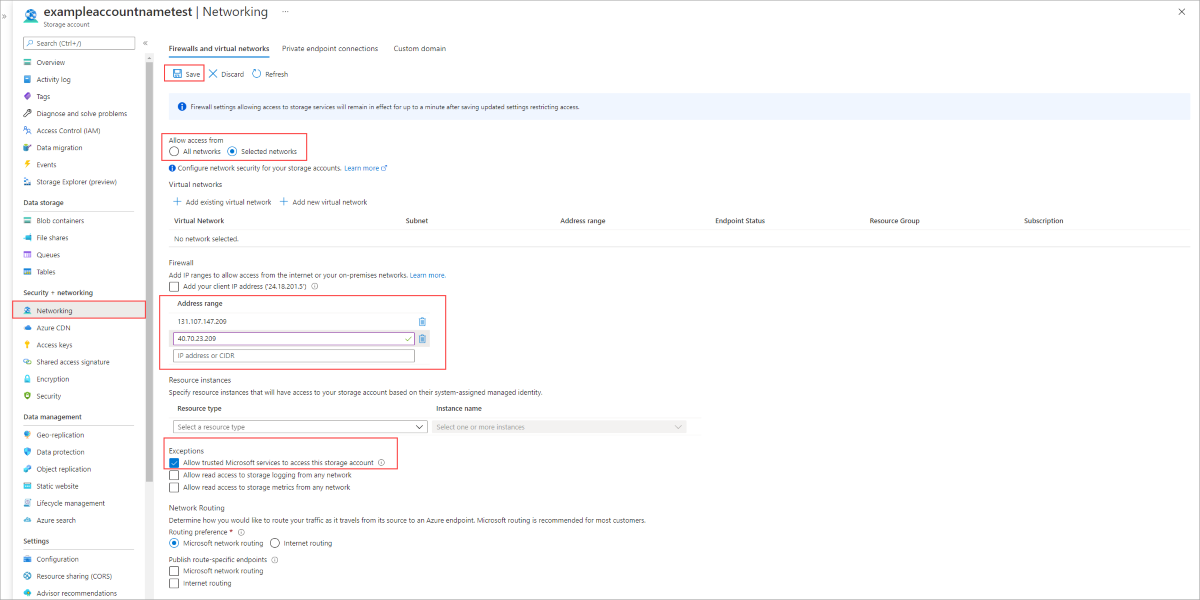
If you'd like to configure your Azure File sync to work with firewall and virtual network settings, do the following:
From the Azure portal, navigate to the storage account you want to secure.
Select Networking on the left menu.
Under Selected networks under Allow access from.
Make sure your servers IP or virtual network is listed under the Address range section.
Make sure Allow trusted Microsoft services to access this storage account is checked.
Select Save to save your settings.
SMB over QUIC on a server endpoint
Although the Azure file share (cloud endpoint) is a full SMB endpoint capable of direct access from the cloud or on-premises, customers that desire accessing the file share data cloud-side often deploy an Azure File Sync server endpoint on a Windows Server instance hosted on an Azure VM. The most common reason to have an additional server endpoint rather than accessing the Azure file share directly is that changes made directly on the Azure file share may take up to 24 hours or longer to be discovered by Azure File Sync, while changes made on a server endpoint are discovered nearly immediately and synced to all other server and cloud-endpoints.
This configuration is extremely common in environments where a substantial portion of users are not on-premises, such as when users are working from home or from the road. Traditionally, accessing any file share with SMB over the public internet, including both file shares hosted on Windows File Server or on Azure Files directly, is very difficult since most organizations and ISPs block port 445. You can work around this limitation with private endpoints and VPNs, however Windows Server 2022 Azure Edition provides an additional access strategy: SMB over the QUIC transport protocol.
SMB over QUIC communicates over port 443, which most organizations and ISPs have open to support HTTPS traffic. Using SMB over QUIC greatly simplifies the networking required to access a file share hosted on an Azure File Sync server endpoint for clients using Windows 11 or greater. To learn more about how to setup and configure SMB over QUIC on Windows Server Azure Edition, see SMB over QUIC for Windows File Server.
Onboarding with Azure File Sync
The recommended steps to onboard on Azure File Sync for the first time with zero downtime while preserving full file fidelity and access control list (ACL) are as follows:
- Deploy a Storage Sync Service.
- Create a sync group.
- Install Azure File Sync agent on the server with the full data set.
- Register that server and create a server endpoint on the share.
- Let sync do the full upload to the Azure file share (cloud endpoint).
- After the initial upload is complete, install Azure File Sync agent on each of the remaining servers.
- Create new file shares on each of the remaining servers.
- Create server endpoints on new file shares with cloud tiering policy, if desired. (This step requires additional storage to be available for the initial setup.)
- Let Azure File Sync agent do a rapid restore of the full namespace without the actual data transfer. After the full namespace sync, sync engine will fill the local disk space based on the cloud tiering policy for the server endpoint.
- Ensure sync completes and test your topology as desired.
- Redirect users and applications to this new share.
- You can optionally delete any duplicate shares on the servers.
If you don't have extra storage for initial onboarding and would like to attach to the existing shares, you can pre-seed the data in the Azure files shares. This approach is suggested, if and only if you can accept downtime and absolutely guarantee no data changes on the server shares during the initial onboarding process.
- Ensure that data on any of the servers can't change during the onboarding process.
- Pre-seed Azure file shares with the server data using any data transfer tool over the SMB. Robocopy, for example. You can also use AzCopy over REST. Be sure to use AzCopy with the appropriate switches to preserve ACLs timestamps and attributes.
- Create Azure File Sync topology with the desired server endpoints pointing to the existing shares.
- Let sync finish reconciliation process on all endpoints.
- Once reconciliation is complete, you can open shares for changes.
Currently, pre-seeding approach has a few limitations -
- Data changes on the server before the sync topology is fully up and running can cause conflicts on the server endpoints.
- After the cloud endpoint is created, Azure File Sync runs a process to detect the files in the cloud before starting the initial sync. The time taken to complete this process varies depending on the various factors like network speed, available bandwidth, and number of files and folders. For the rough estimation in the preview release, detection process runs approximately at 10 files/sec. Hence, even if pre-seeding runs fast, the overall time to get a fully running system may be significantly longer when data is pre-seeded in the cloud.
Self-service restore through Previous Versions and VSS (Volume Shadow Copy Service)
Important
The following information can only be used with version 9 (or above) of the storage sync agent. Versions lower than 9 will not have the StorageSyncSelfService cmdlets.
Previous Versions is a Windows feature that allows you to utilize server-side VSS snapshots of a volume to present restorable versions of a file to an SMB client. This enables a powerful scenario, commonly referred to as self-service restore, directly for information workers instead of depending on the restore from an IT admin.
VSS snapshots and Previous Versions work independently of Azure File Sync. However, cloud tiering must be set to a compatible mode. Many Azure File Sync server endpoints can exist on the same volume. You have to make the following PowerShell call per volume that has even one server endpoint where you plan to or are using cloud tiering.
Import-Module '<SyncAgentInstallPath>\StorageSync.Management.ServerCmdlets.dll'
Enable-StorageSyncSelfServiceRestore [-DriveLetter] <string> [[-Force]]
VSS snapshots are taken of an entire volume. By default, up to 64 snapshots can exist for a given volume, granted there is enough space to store the snapshots. VSS handles this automatically. The default snapshot schedule takes two snapshots per day, Monday through Friday. That schedule is configurable via a Windows Scheduled Task. The above PowerShell cmdlet does two things:
- It configures Azure File Syncs cloud tiering on the specified volume to be compatible with previous versions and guarantees that a file can be restored from a previous version, even if it was tiered to the cloud on the server.
- It enables the default VSS schedule. You can then decide to modify it later.
Note
There are two important things to note:
- If you use the -Force parameter, and VSS is currently enabled, then it will overwrite the current VSS snapshot schedule and replace it with the default schedule. Ensure you save your custom configuration before running the cmdlet.
- If you are using this cmdlet on a cluster node, you must also run it on all the other nodes in the cluster!
In order to see if self-service restore compatibility is enabled, you can run the following cmdlet.
Get-StorageSyncSelfServiceRestore [[-Driveletter] <string>]
It will list all volumes on the server as well as the number of cloud tiering compatible days for each. This number is automatically calculated based on the maximum possible snapshots per volume and the default snapshot schedule. So by default, all previous versions presented to an information worker can be used to restore from. The same is true if you change the default schedule to take more snapshots. However, if you change the schedule in a way that will result in an available snapshot on the volume that is older than the compatible days value, then users will not be able to use this older snapshot (previous version) to restore from.
Note
Enabling self-service restore can have an impact on your Azure storage consumption and bill. This impact is limited to files currently tiered on the server. Enabling this feature ensures that there is a file version available in the cloud that can be referenced via a previous versions (VSS snapshot) entry.
If you disable the feature, the Azure storage consumption will slowly decline until the compatible days window has passed. There is no way to speed this up.
The default maximum number of VSS snapshots per volume (64) as well as the default schedule to take them, result in a maximum of 45 days of previous versions an information worker can restore from, depending on how many VSS snapshots you can store on your volume.
If a maximum of 64 VSS snapshots per volume is not the correct setting for you, then change that value via a registry key. For the new limit to take effect, you need to re-run the cmdlet to enable previous version compatibility on every volume it was previously enabled, with the -Force flag to take the new maximum number of VSS snapshots per volume into account. This will result in a newly calculated number of compatible days. Please note that this change will only take effect on newly tiered files and overwrite any customizations on the VSS schedule you might have made.
Proactively recall new and changed files from an Azure file share
With agent version 11, a new mode becomes available on a server endpoint. This mode allows globally distributed companies to have the server cache in a remote region pre-populated even before local users are accessing any files. When enabled on a server endpoint, this mode will cause this server to recall files that have been created or changed in the Azure file share.
Scenario
A globally distributed company has branch offices in the US and in India. In the morning (US time) information workers create a new folder and new files for a brand new project and work all day on it. Azure File Sync will sync folder and files to the Azure file share (cloud endpoint). Information workers in India will continue working on the project in their timezone. When they arrive in the morning, the local Azure File Sync enabled server in India needs to have these new files available locally, such that the India team can efficiently work off of a local cache. Enabling this mode prevents the initial file access to be slower because of on-demand recall and enables the server to proactively recall the files as soon as they were changed or created in the Azure file share.
Important
It is important to realize that tracking changes in the Azure file share that closely on the server can increase your egress traffic and bill from Azure. If files recalled to the server are not actually needed locally, then unnecessary recall to the server can have negative consequences. Use this mode when you know pre-populating the cache on a server with recent changes in the cloud will have a positive effect on users or applications using the files on that server.
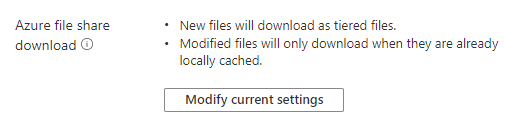
Enable a server endpoint to proactively recall what changed in an Azure file share
- In the Azure portal, go to your Storage Sync Service, select the correct sync group and then identify the server endpoint for which you want to closely track changes in the Azure file share (cloud endpoint).
- In the cloud tiering section, find the "Azure file share download" topic. You will see the currently selected mode and can change it to track Azure file share changes more closely and proactively recall them to the server.
Migrate a DFS Replication (DFS-R) deployment to Azure File Sync
To migrate a DFS-R deployment to Azure File Sync:
- Create a sync group to represent the DFS-R topology you are replacing.
- Start on the server that has the full set of data in your DFS-R topology to migrate. Install Azure File Sync on that server.
- Register that server and create a server endpoint for the first server to be migrated. Do not enable cloud tiering.
- Let all of the data sync to your Azure file share (cloud endpoint).
- Install and register the Azure File Sync agent on each of the remaining DFS-R servers.
- Disable DFS-R.
- Create a server endpoint on each of the DFS-R servers. Do not enable cloud tiering.
- Ensure sync completes and test your topology as desired.
- Retire DFS-R.
- Cloud tiering may now be enabled on any server endpoint as desired.
For more information, see Azure File Sync interop with Distributed File System (DFS).
Comments